MD-NEXT v1.90.3 ~ v1.90.11
- Android Full Filesystem extraction for Android 11 Galaxy A series – Supports A10, A11, A30, A40, A50, Jean2, Wide4 series.
- Increased iOS FFS extraction success ratio by improving the stability of Checkm8 method
- Supports ‘Before First Unlock(BFU)’ extraction process when screen lock can’t be unlocked.
- Supports HiSuite backup protocol for the devices with Android 10 or higher versions
- Improved App Downgrade and Restoring process for Samsung Android version 11 or above
MD-RED v3.7.37 ~ v3.7.48
- Supports analysis of Recycle Bin in Samsung devices with Android 11
- Nokia feature phone analysis: TA-1017, TA-1034
- Improved metadata analysis of image/video – MD-RED displays the time zone information next to the date/time
- Supports ‘Unclassified file’ artifacts
- Supports batch checking of related chat room/contact from the analysis results
MD-LIVE v3.4.4 ∼ v3.4.7
- Supports Video/Audio recording by HDMI capture card
- Supports DB Report (SQLite)
- Supports HiSuite backup protocol for the devices with Android 10 or higher versions
- Added Keywords Search by Regular Expression
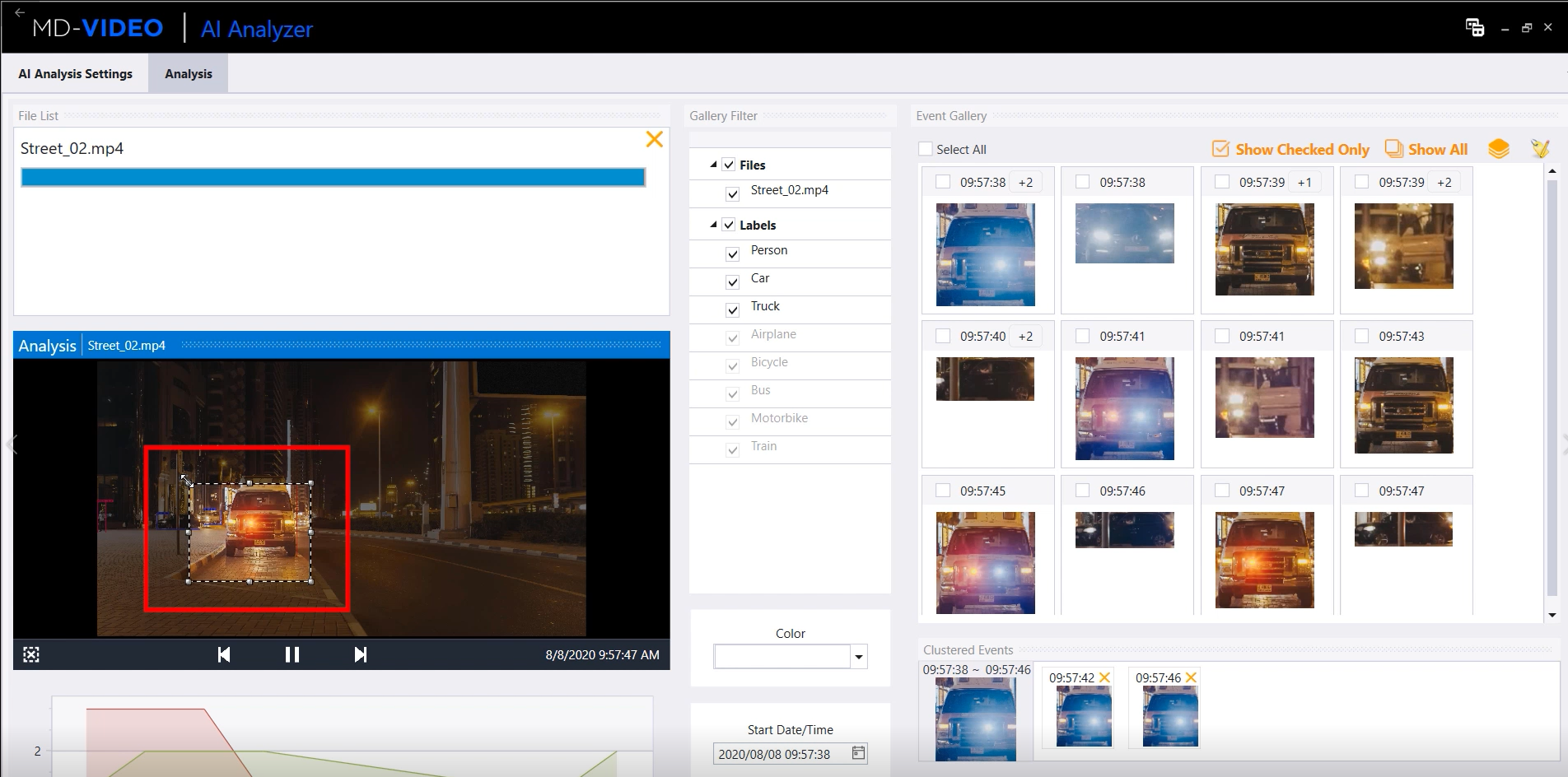
MD-VIDEO v3.7.0 ∼ v3.7.2
- Supports video recovery from the file slack area of FAT32-based format free filesystem
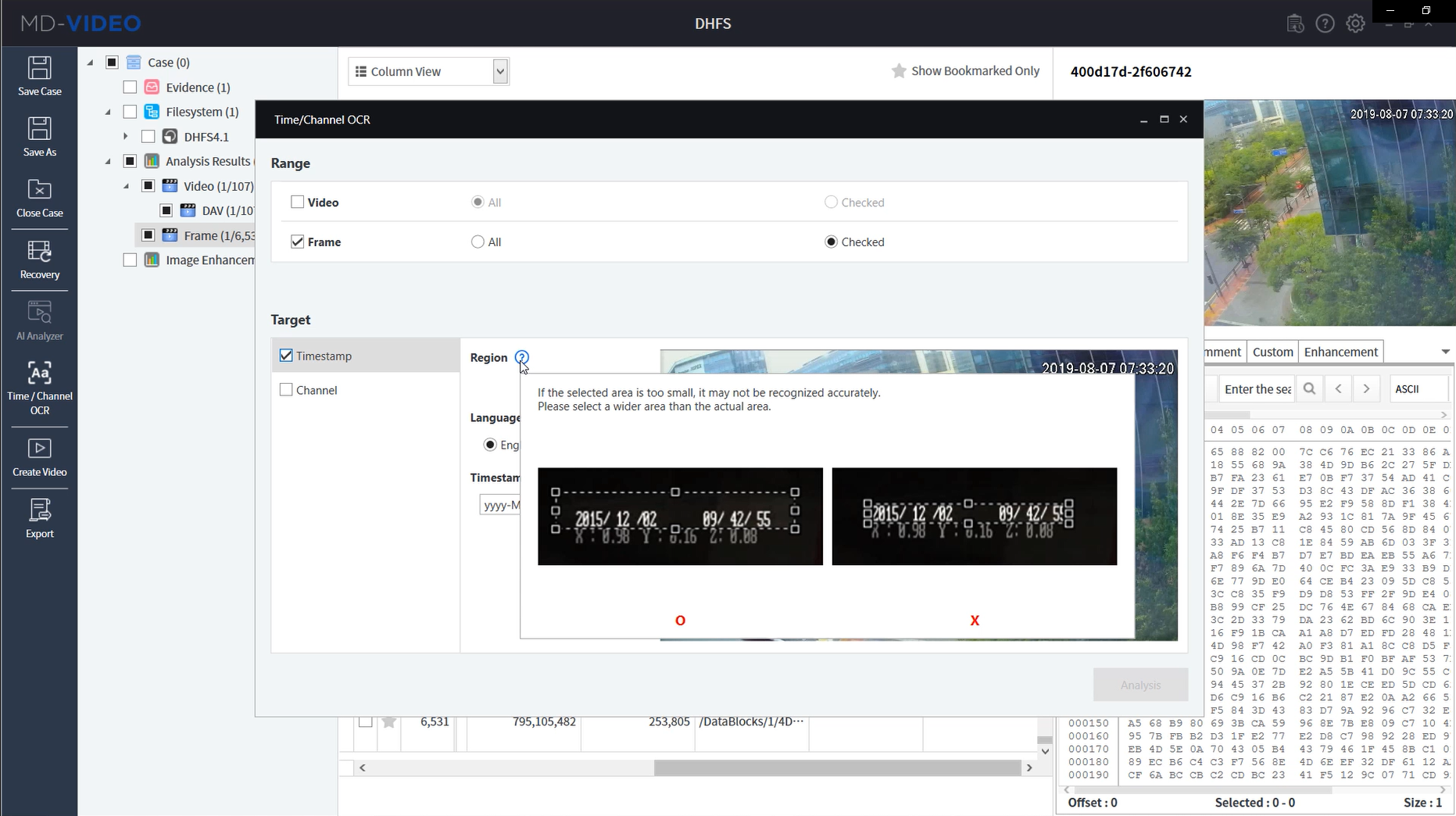
- Supports automatic detection of bounding box of each digit in the selected area
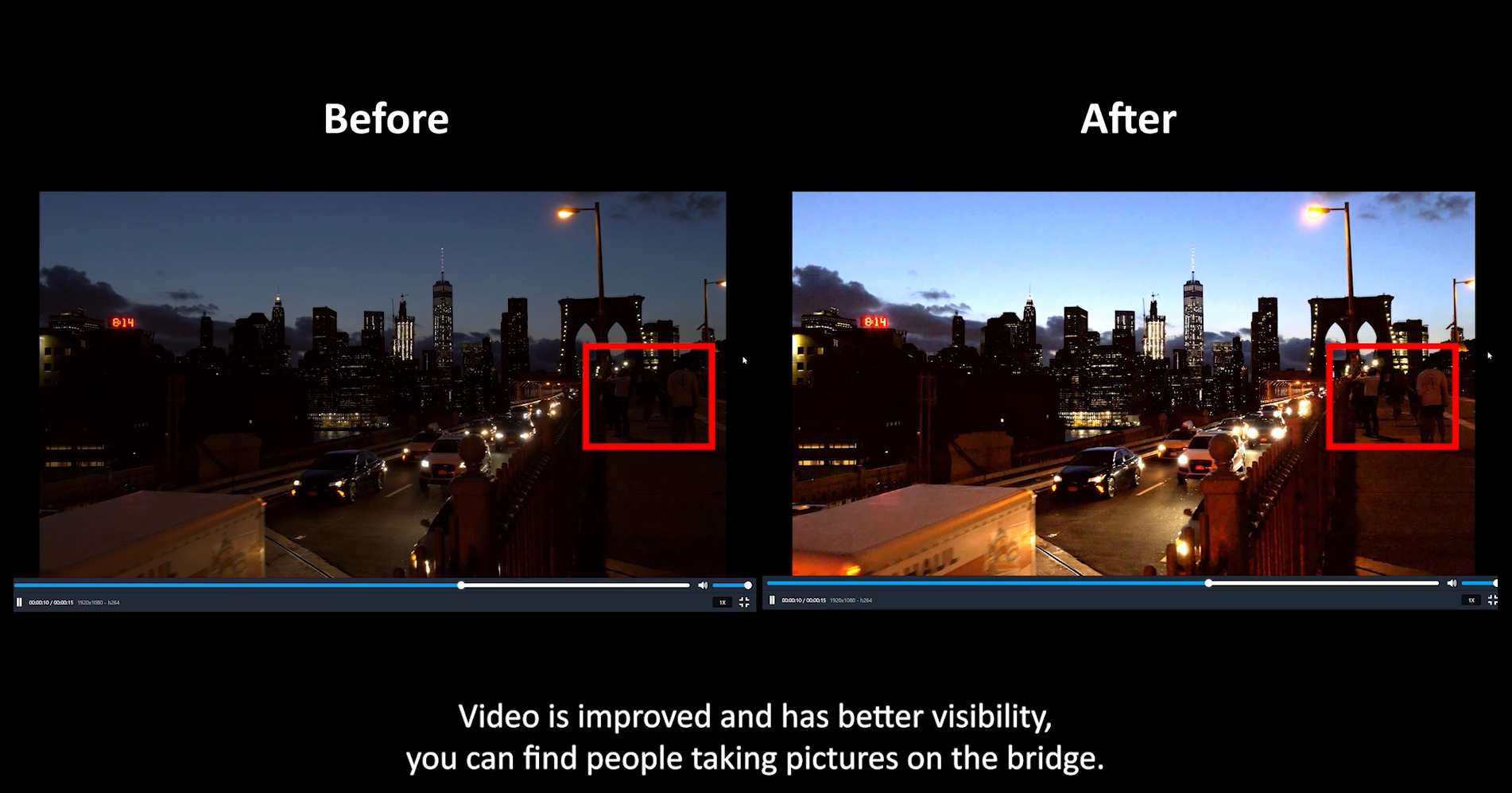
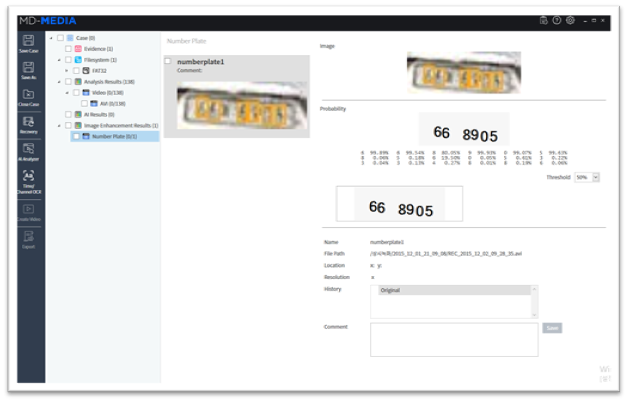
- Improvements of MD-VIDEO AI – Timeline UI/UX, Added SRGAN model for super-resolution, Number Plate Analysis, Viewer UI, Comments UI
- Added new models – DVR(5), Dashcam(5)
-DVR: Hanwha Techwin (XRN-1610A), ITX Security (UTM5HGB), NADATEL (AP-0405R), WEBGATE (HAC430F)
-Dashcam: Apeman (C450), COMTEC (ZDR-015), Garmin (66W), KENWOOD (DRV-MR745), Nextbase (622GW)
MD-CLOUD v1.7.0
- Improved analysis of recurring information in Google Calendar
- Enhanced preview function by adding additional media formats
Download the full release note highlights!