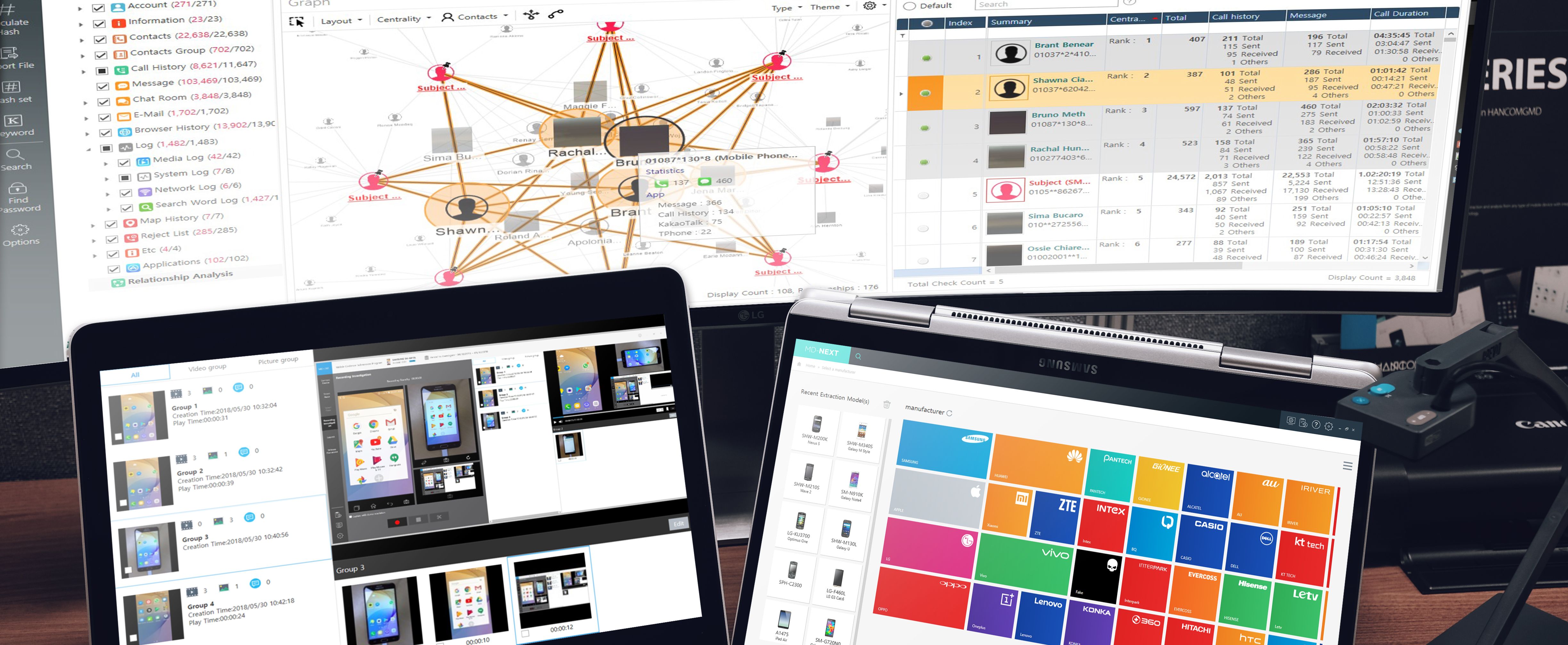
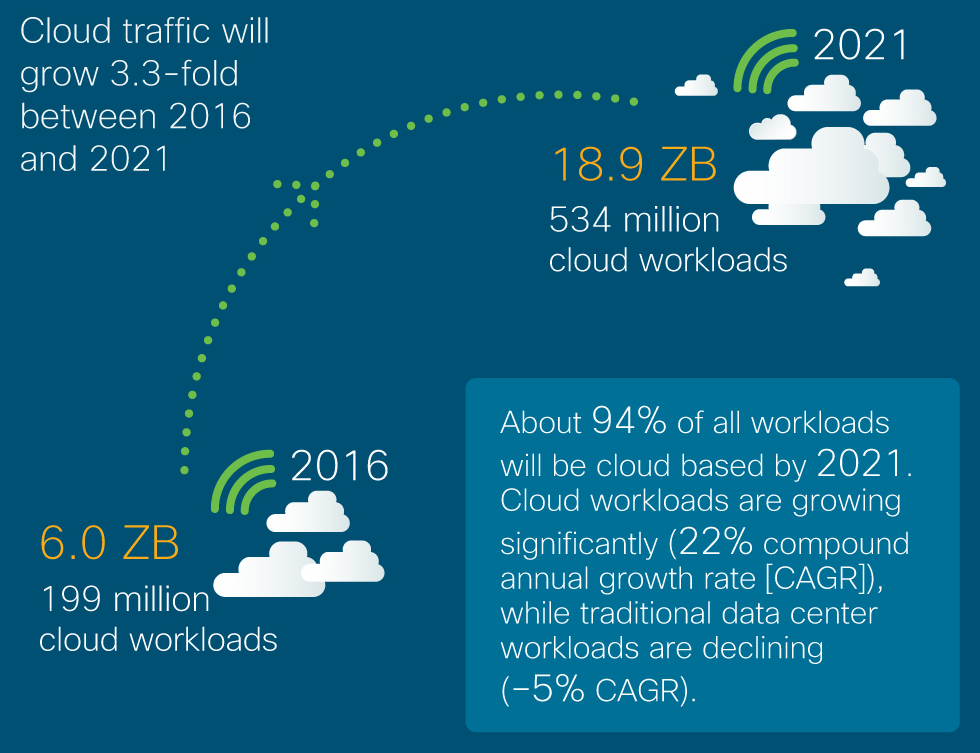
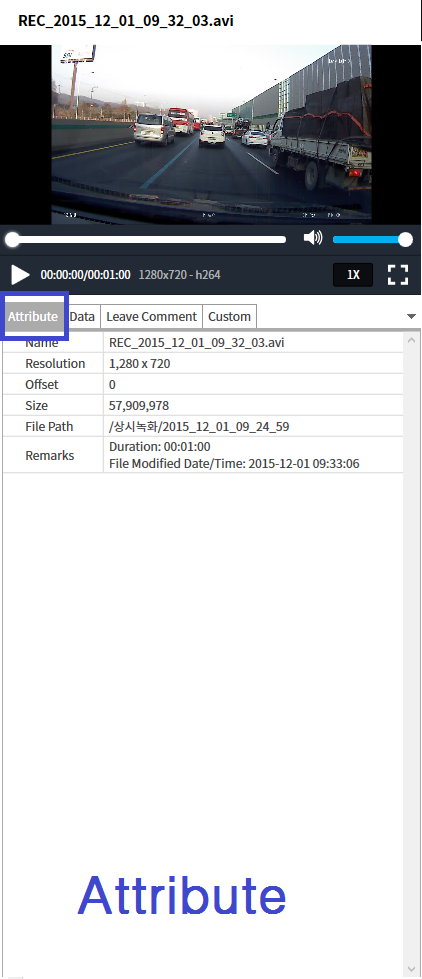
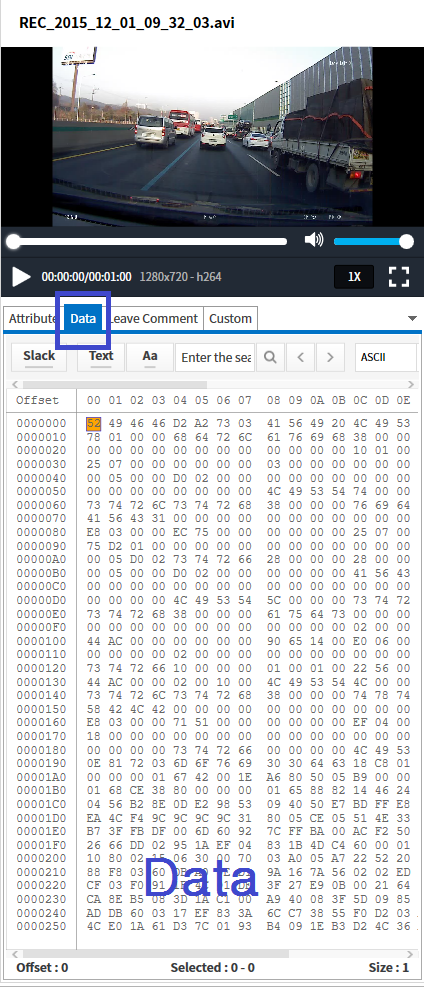
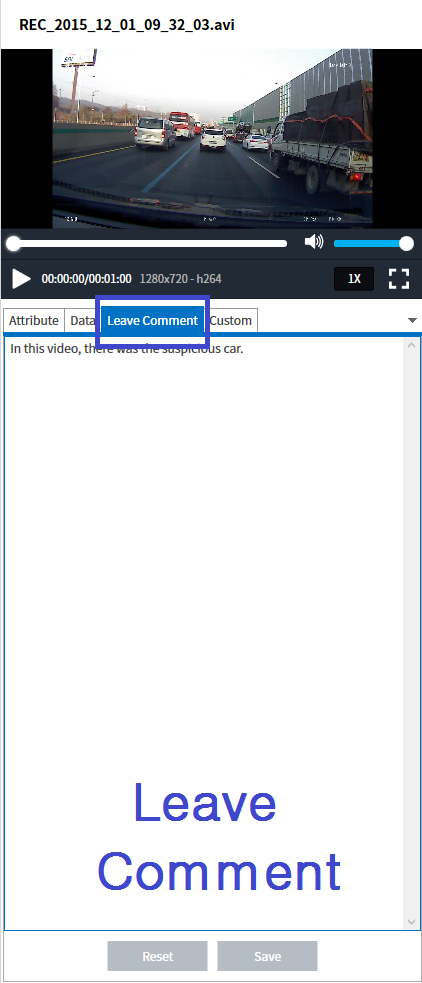
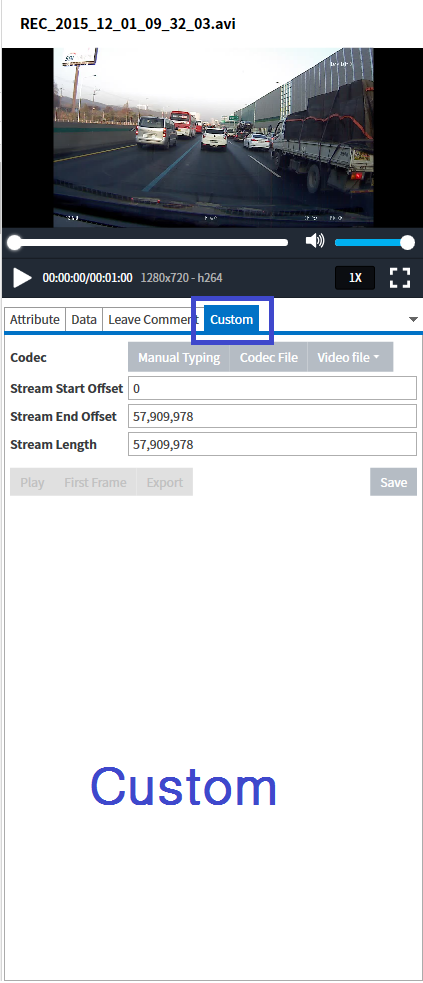
2Q 2020 MD-Series Release Note Highlights
Check the major features of MD-Series released in 2Q 2020, if you would like to know more go download PDF file.
MD-NEXT v1.88.1-1.89.4
- New iOS Full Filesystem(Checkm8) Extraction applied to iPhone series SE/6s/6s+/7/7+/8/8+/X
- New Physical Extraction for Samsung Galaxy Exynos Chipset, Android 10
- Bootloader Pro Extraction supports the latest version of Android 10
- Unlock support for Xiaomi models with MIUI 10 to 11
MD-RED v3.5.3-3.6.8
- Added Report Exporting feature for ‘MD-Explorer’ viewer program
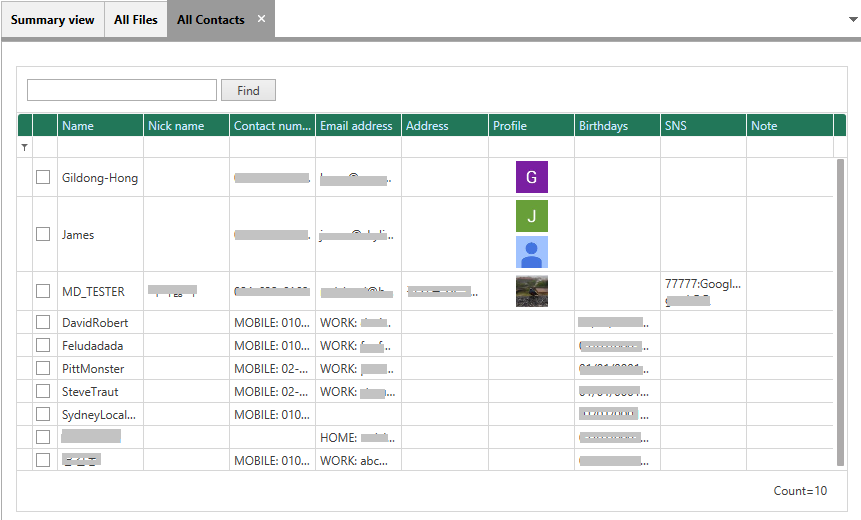
- Analysis of Samsung Secure Folder
- Analysis support for iOS Full Filesystem image format from Cellebrite ‘UFED’ (*.dar)
- iOS Full File System (Added system logs analysis)
- Supports analysis for Android apps installed in Parallel Space app
MD-LIVE v3.3.10-3.3.14
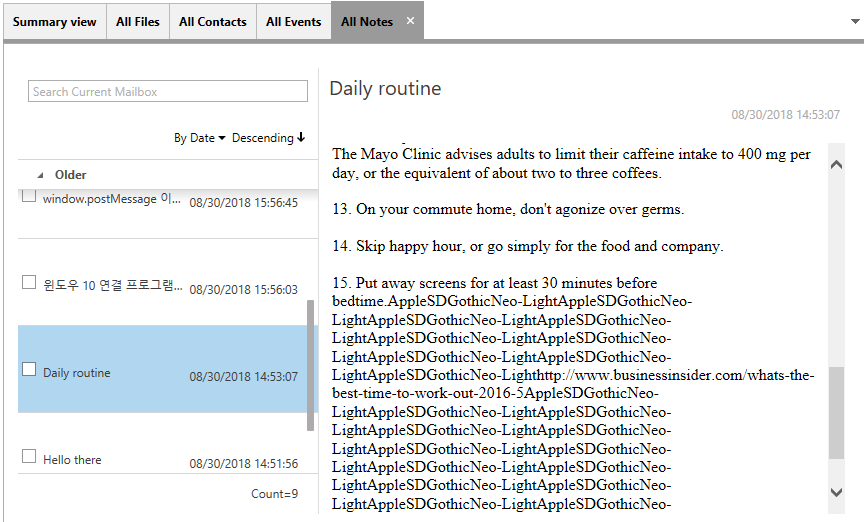
- New Device Log Analysis Feature
- Supports analysis for Android apps installed in Parallel Space app
- User can decide proceeding downgrade according to the state of app installation
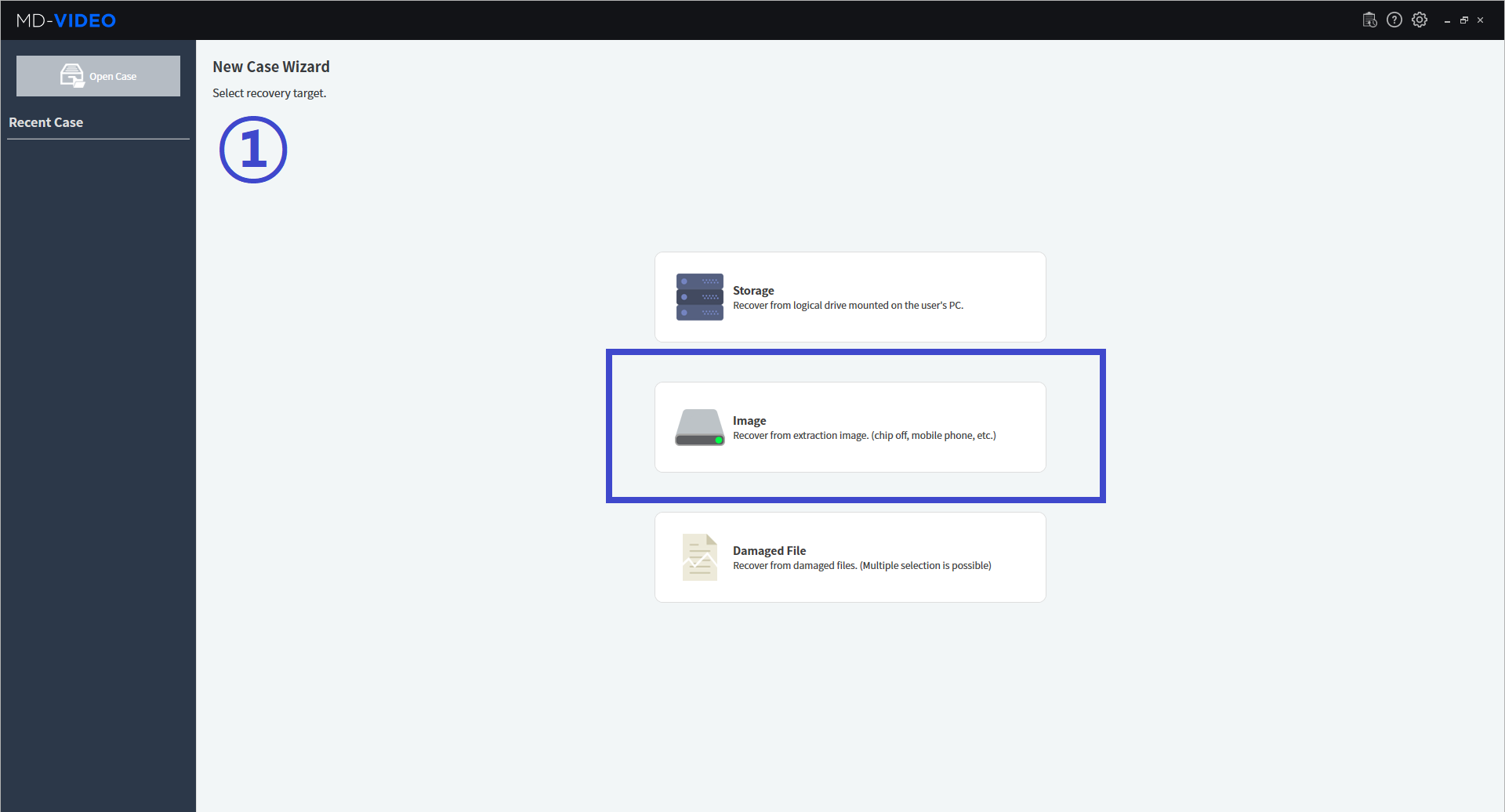
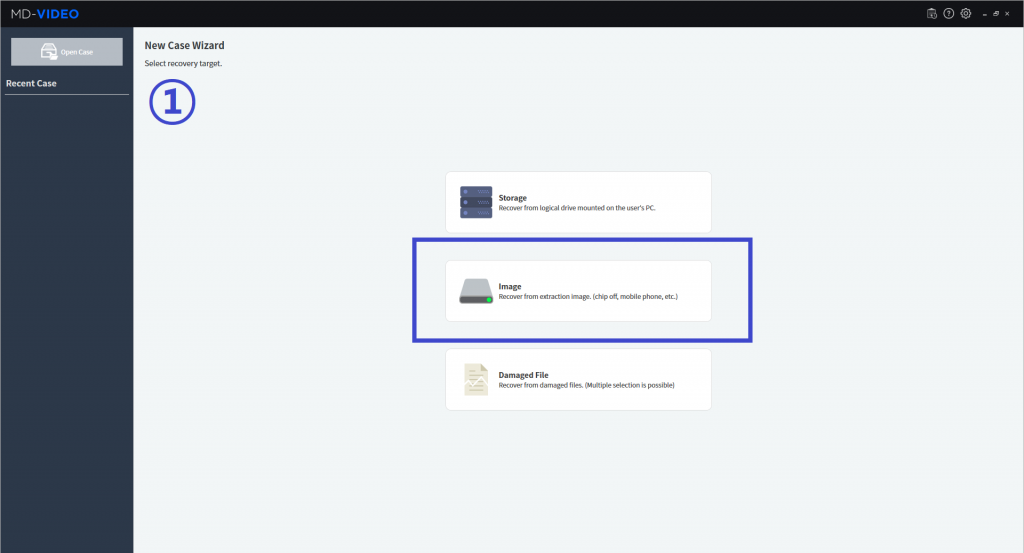
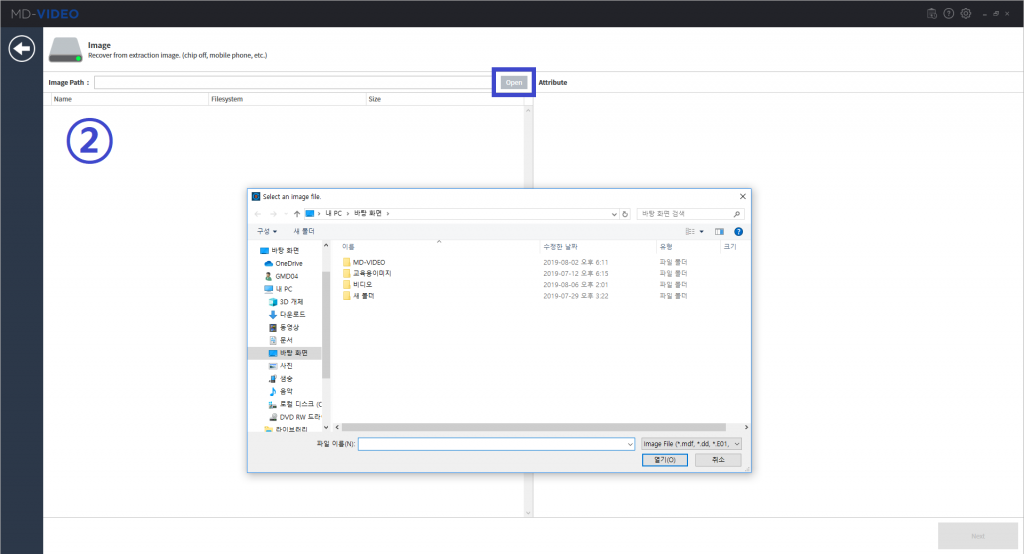
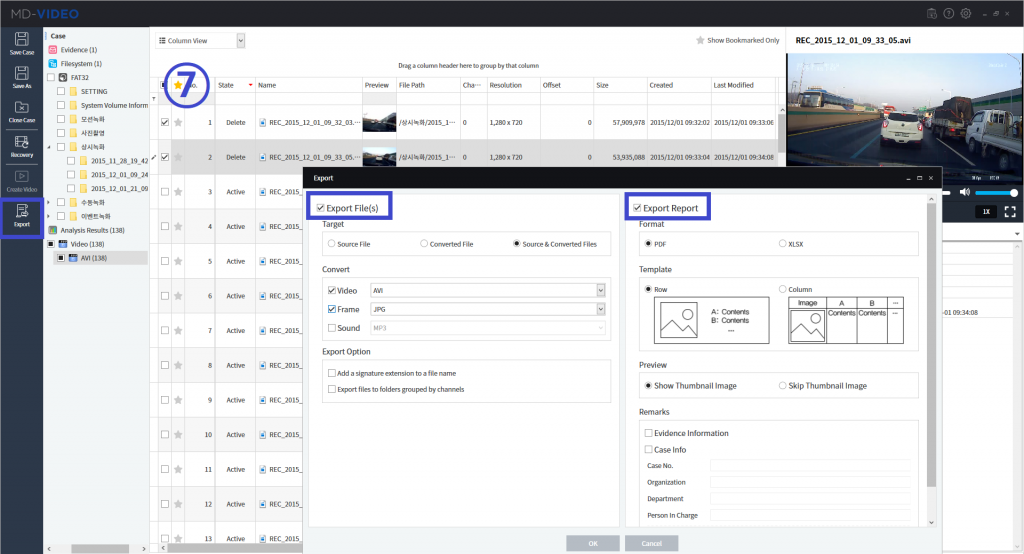
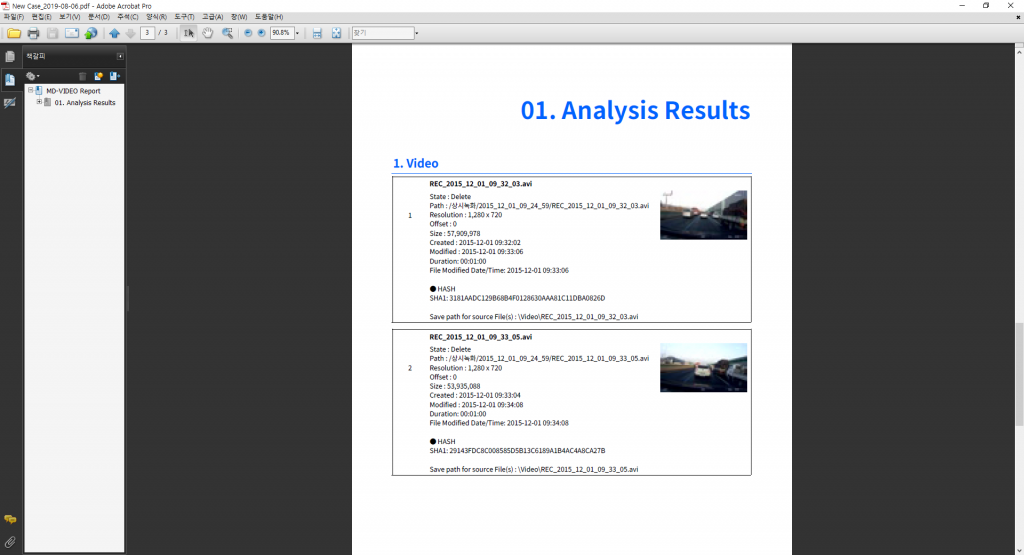
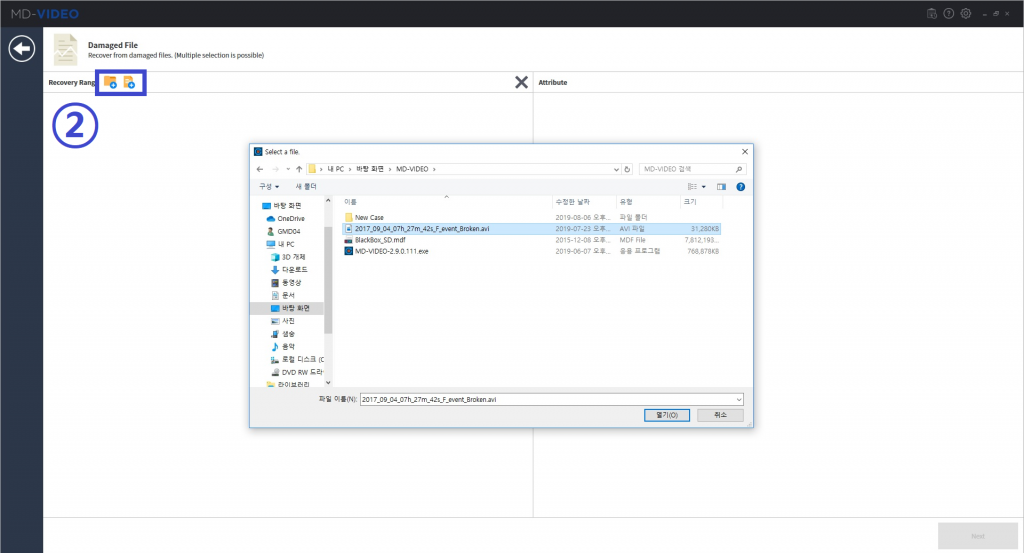
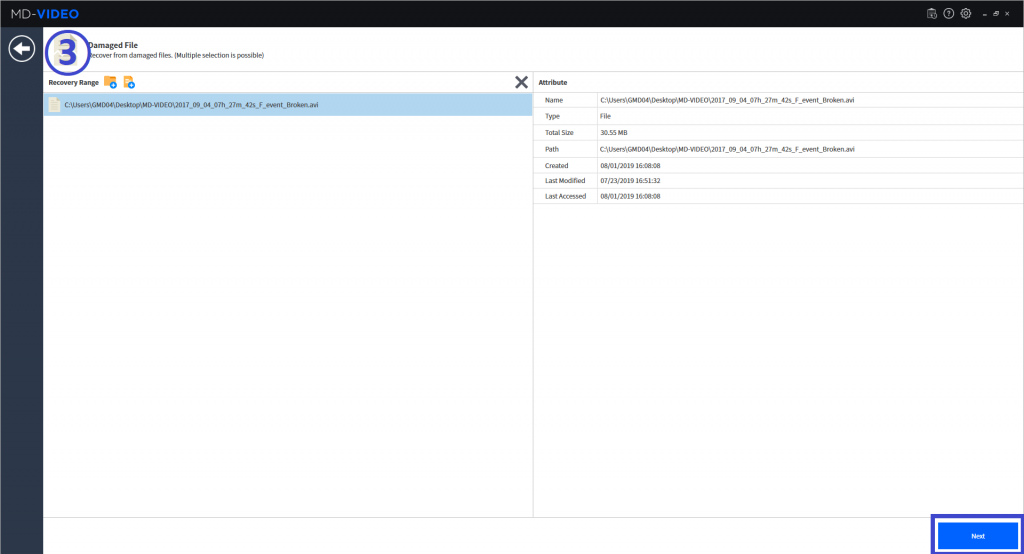
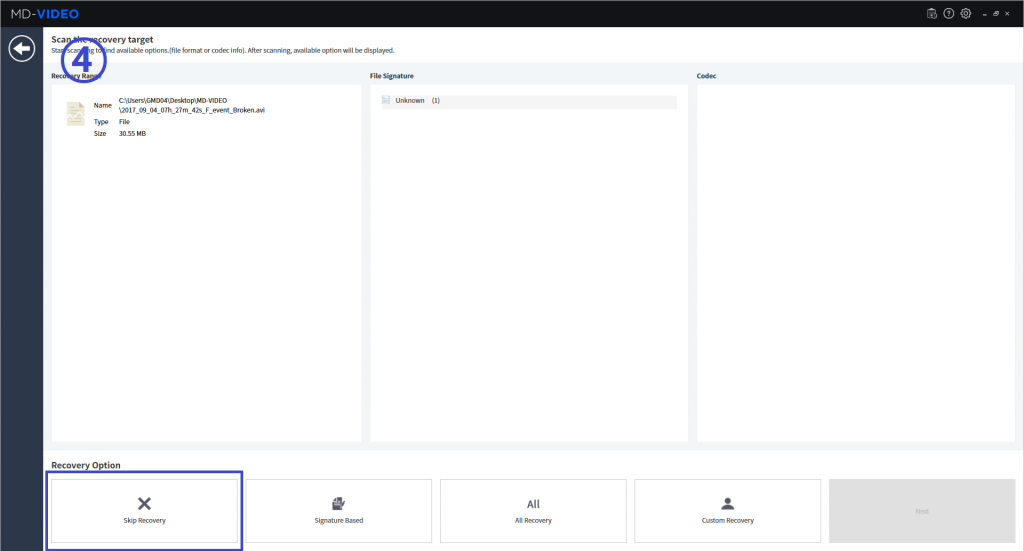
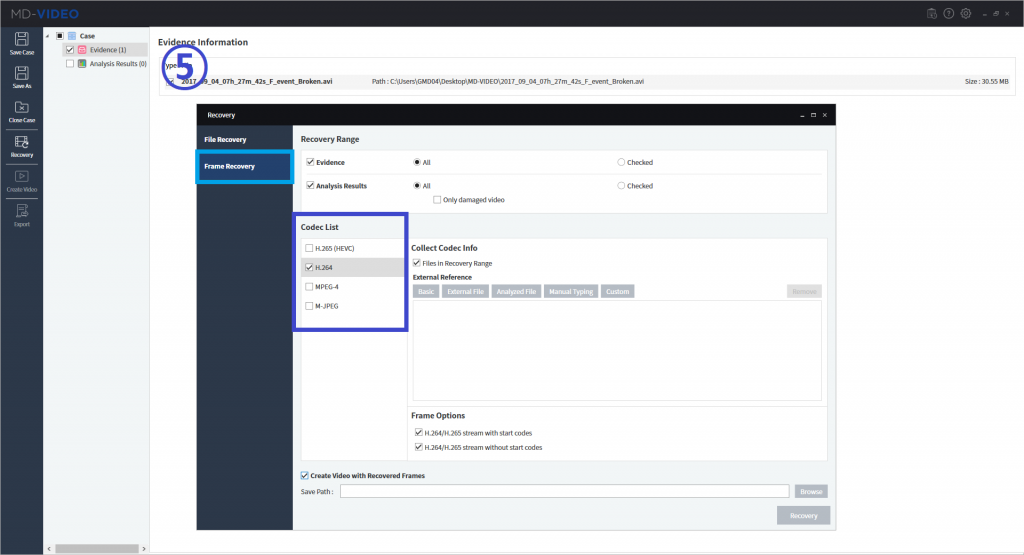
MD-VIDEO v3.1.0-3.2.0
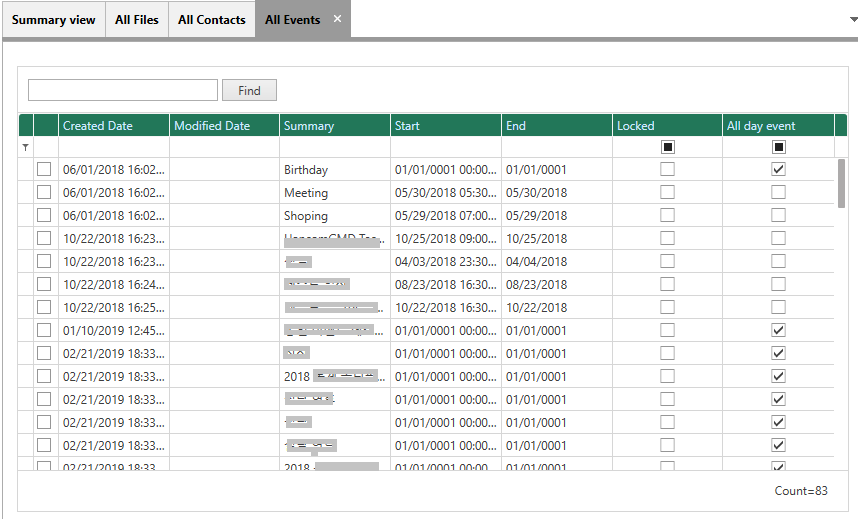
- Resume the abnormally terminated case
- The image can be enhanced by adjusting the brightness, contrast, and color of the analysis results
- AI Analysis has added function that allows users to filter only the objects matched by the selected area and by the selected color in the Object Gallery
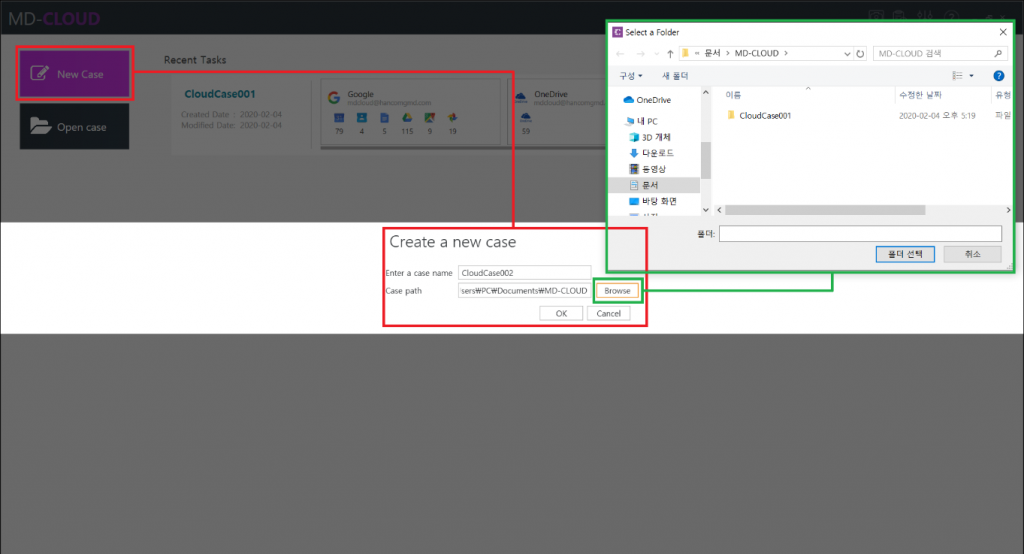
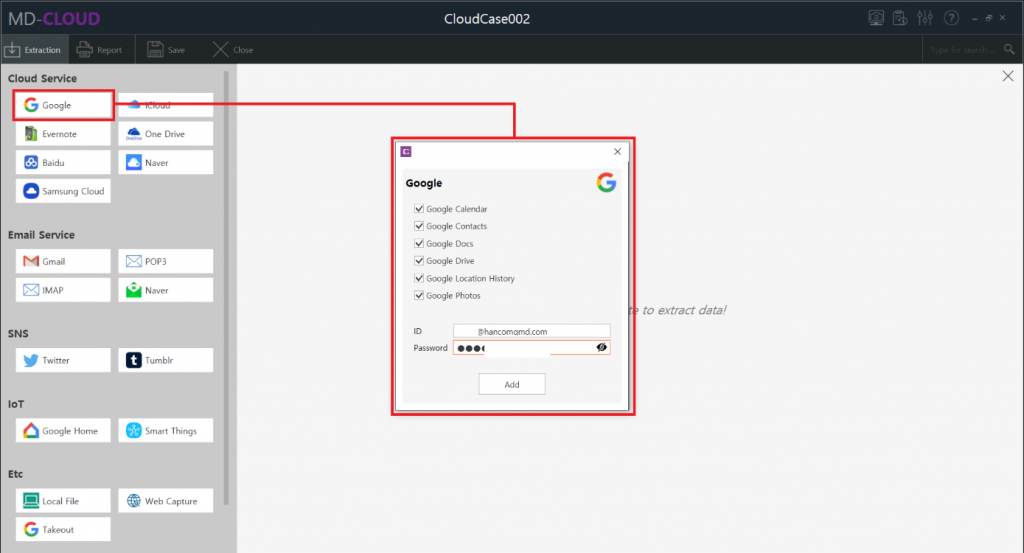
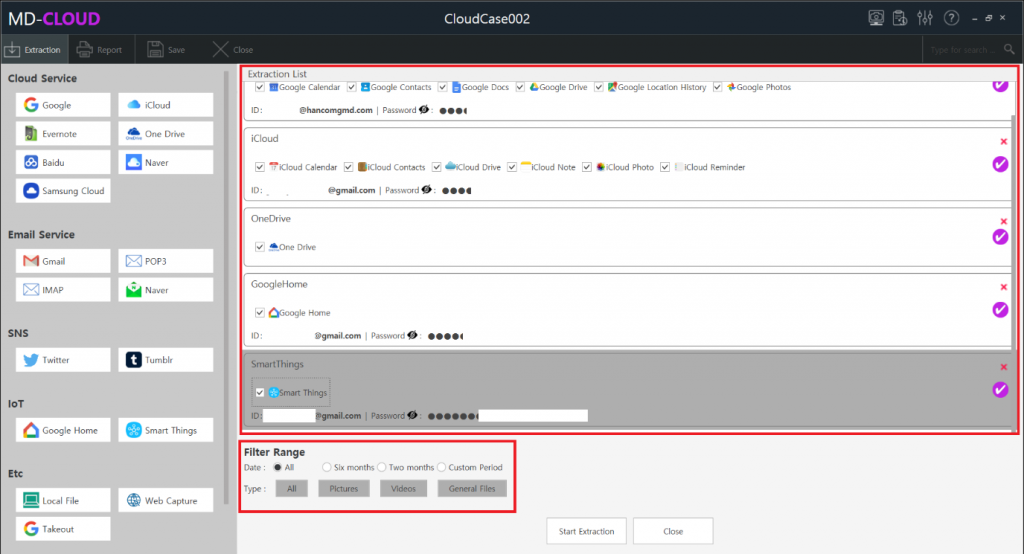
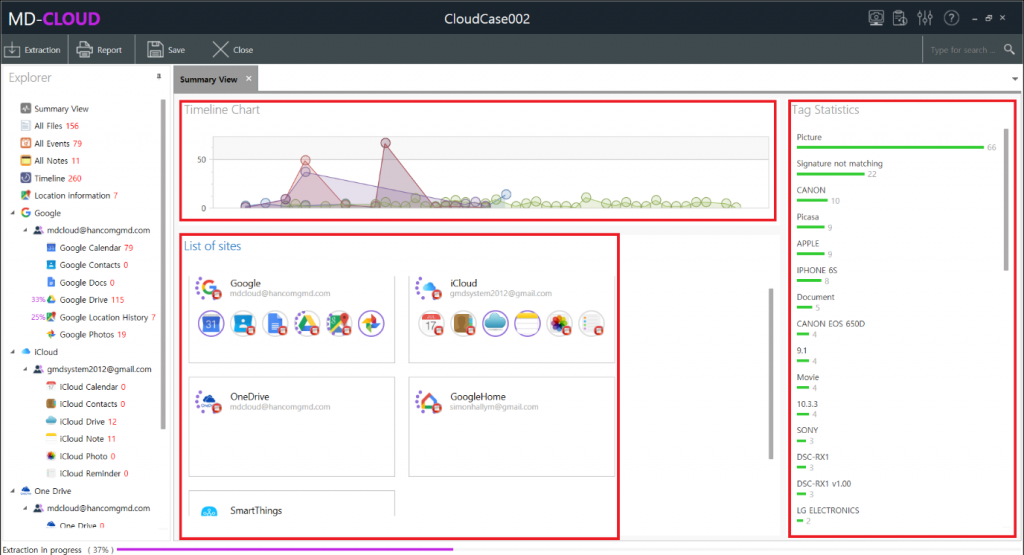
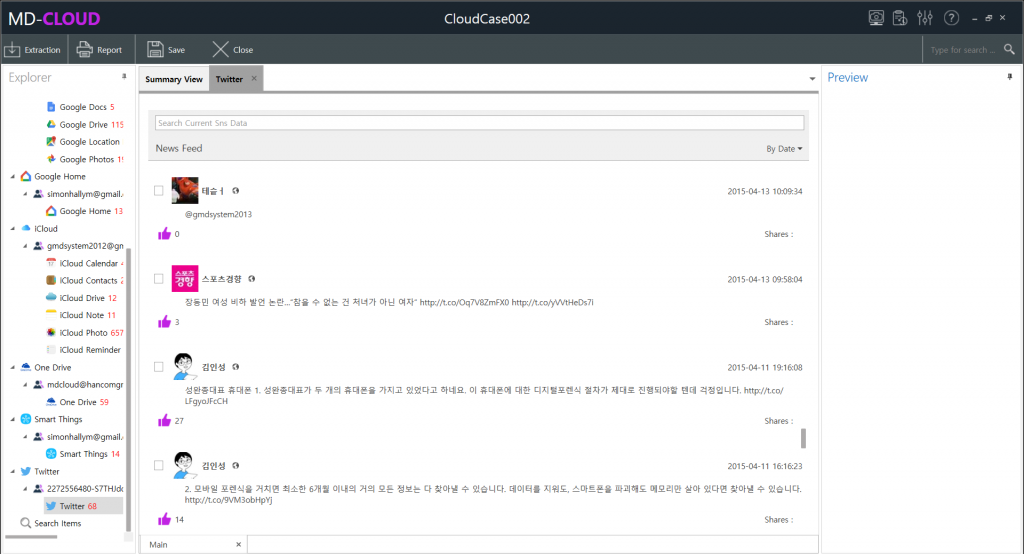
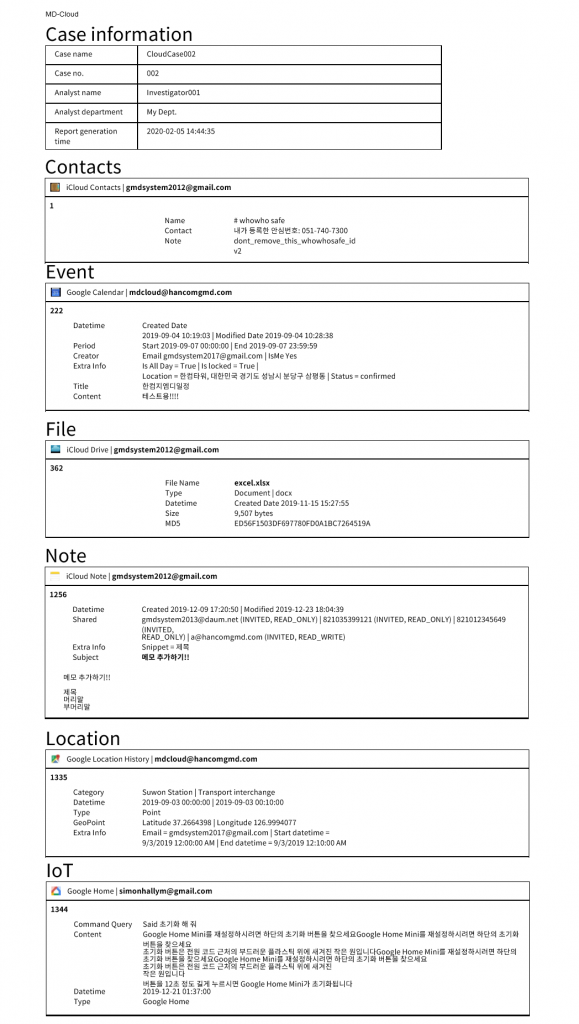
MD-CLOUD v1.3.0
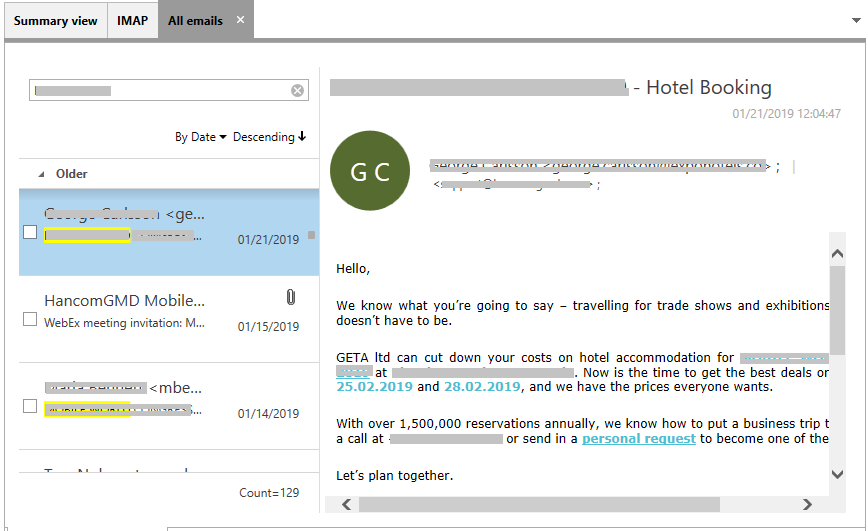
- Added ‘Telegram’ extraction module – Credential file authentication (Android), Mobile authentication (Android, iOS, etc.)
Download PDF File – Releasenote 2Q 2020 Final
1Q 2020 MD-Series Release Note Highlights
Check the major features of MD-Series released in 1Q 2020, if you would like to know more go download PDF file.
MD-NEXT -v1.88.0
Screen Unlock and physical extraction methods for Android devices and Full Filesystem extraction for iOS have released. These features will allow users to access and extract more data from a wide range of Android devices, devices with MediaTek chipset, and Samsung Secure Folder.
MD-RED v3.4.17-3.5.2
Filters for multimedia are supported; ‘Attribute Filter’ and ‘Path Filter’. These new filters allow users to investigate more time efficiently by filtering the multimedia data by its’ type and path.
MD-LIVE v3.3.3-3.3.9
Hash verification and app downgrade extraction support for Android are released in MD-LIVE. Hash verification feature will allow users to manage criminal evidence-related file list via hash and quickly find harmful files during the analysis process.
MD-VIDEO v2.10.0-3.0.0
TAT32, WFS0.4 fllesystem analysis is available for MD-VIDEO, and ‘Region Filter’ and ‘Time Filter’ are added in MD-VIDEO AI analysis.
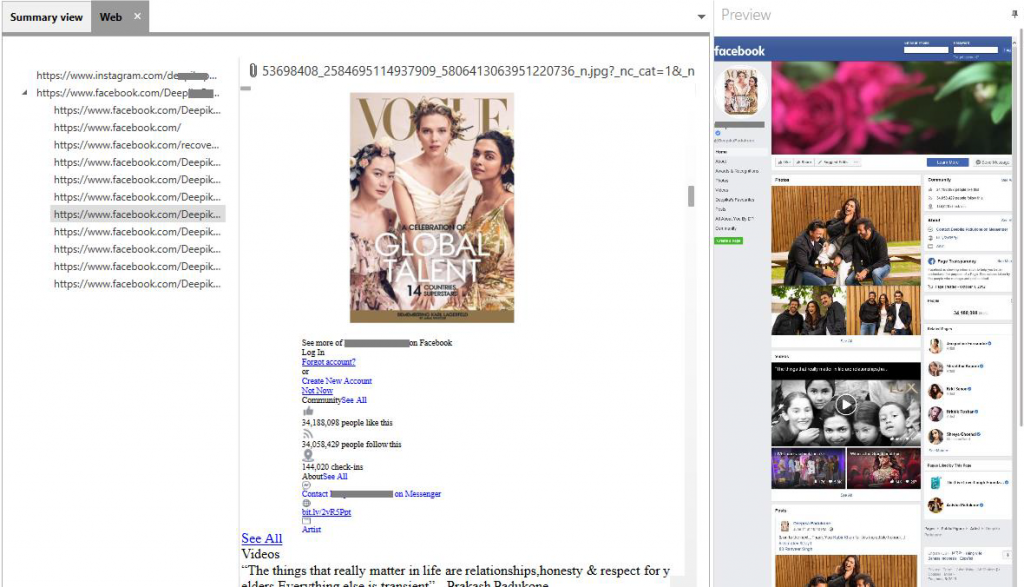
MD-CLOUD v1.2.0
Cloud data from GoogleHome and SamsungThings are supported. Users can extract and analyze IoT Device information and activity data from those sources.
Download PDF File – Releasenote_1Q_2020_Final