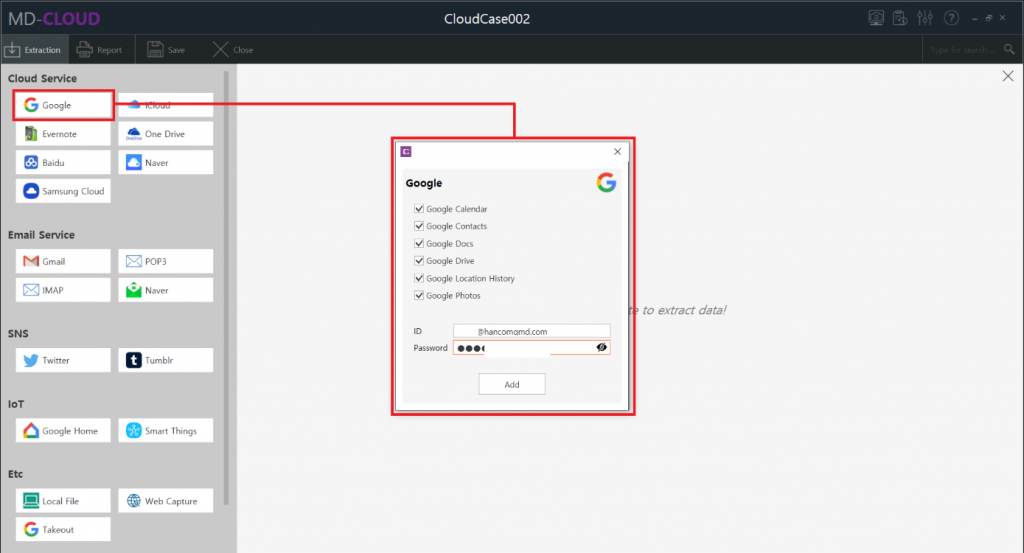
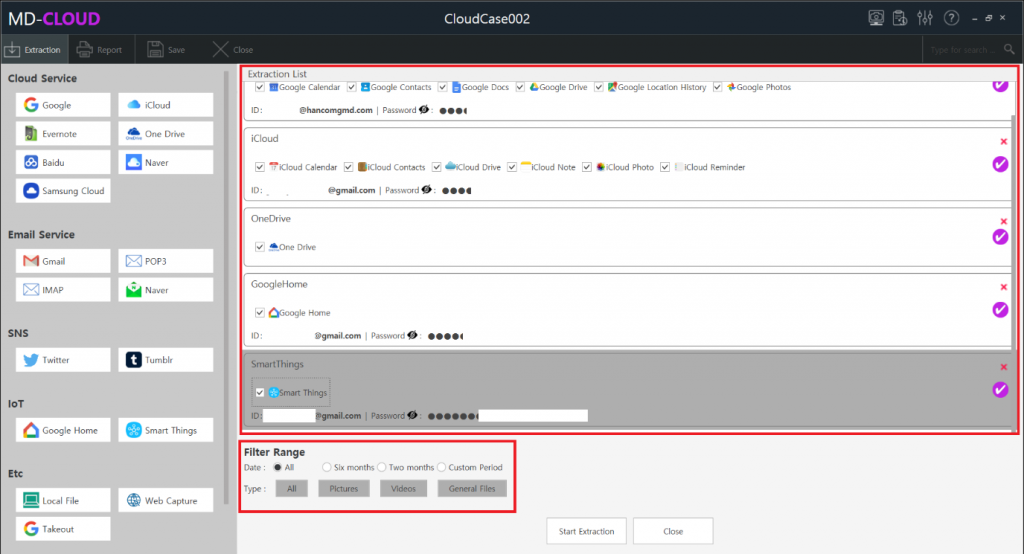
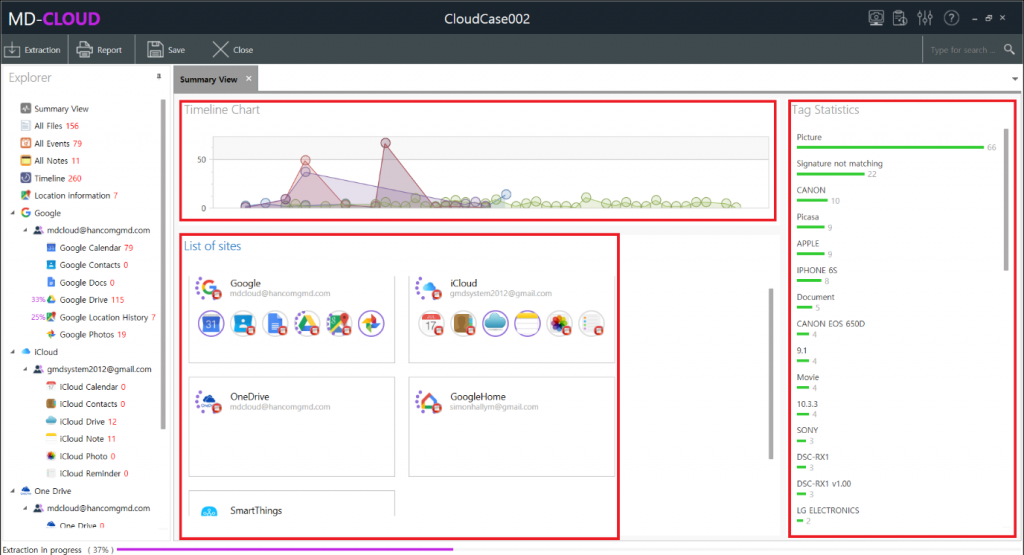
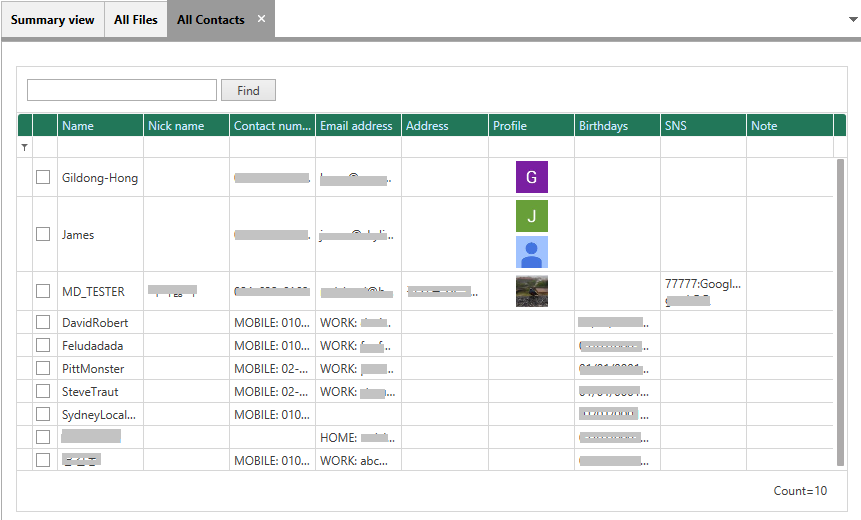
How MD-VIDEO AI can perform the world’s best gun recognition feature?
Recognizing guns with AI technology can be roughly divided into two stages: Learning and Reasoning.
At the learning stage, we train the computer with a large amount of image data, and as a result, get a model that can identify a gun. Then at the reasoning stage which the computer already has gun models, the computer determines whether or not a gun is present in the input image.
Here, what really matters is the learning phase. To make a good model, we need to have a large number of gun images. It also needs to determine whether or not there is a gun in the input image, even if the image is too dark, too bright, small, poor quality, blurred, or partially hidden.
In order to perform good recognition, you need to have a variety of training data. However, getting a large scale of various gun images is limited, it’s not easy to build training data.
So our research team brought up an idea, what if the computer automatically creates the training data and even automatically labels the guns? We can get a really large amount of gun data. Having a lot of data increases the accuracy of gun recognition, it can respond to various input image environments and quality.
To this end, we built a virtual gun image rendering platform by researching and developing the following technologies.
– 3D modeling of 10 pistols and 11 long guns.
– 3D modeling of a hand holding a gun.
– 3D modeling of a total of 4 backgrounds: Parking lot, School, Market, and Construction site.
– Variety of gun placement techniques in the background.
– Technique for placing a part of the gun to be hidden on an object.
– Random parameter adjustment technology such as camera distance, angle, brightness, blur, and shade.
– A technique for accurately labeling parts of a gun in a rendered image (Calculated in pixels).






Based on this, 200,000 virtual gun images were created, and a gun recognition model was created by training with real gun images. Having a lot of data increases the accuracy of gun recognition, it can respond to various input image environments and quality.
Throughout this effort, MD-VIDEO AI could perform the world’s best gun recognition feature among video forensic tools.
Find out more useful features that can empower your investigation.
If you have any support from our team, submit your inquiry!